
A second vulnerability related to the Apache Log4j was discovered on Tuesday after cybersecurity experts reported Days spent To try to correct or reduce the effect of CVE-2021-44228.
News description CVE 2021-45046 Indicates that the correction of CVE-2021-44228 “Some configurations are incomplete” in Apache Log4j 2.15.0.
“When logging configuration uses a different pattern layout than the default context lookup (for example, $$ ctx: loginId}) or the thread context it allows to control the attackers on the Thread Context Map (MDC) input data using the JNDI lookup sample CVE Explanation states that the result of% X,% mdc, or% MDC) is denial of service (DOS).
As the CVE says, Apache Already published Solution to the last issue: Log4j 2.16.0.
The original bug in Log4j, the Java library for logging error messages in applications, has been making headlines since last week. Attacks Launched on December 1st, Salon Cloudflare
There is the Dutch National Cyber Security Center (NCSC-NL) Published A long list of software affected by vulnerability.
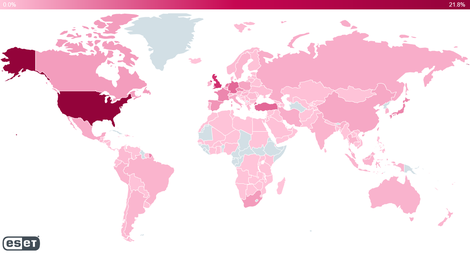
ESET has published a map of countries with attempts to use Log4j with the largest volume in the US, UK, Turkey, Germany and the Netherlands.
ESET
“The size of our detectives confirms that this is a large-scale problem that will never go away. Attackers are sure to test many types of exploitation, but not all attempts are necessarily harmful. Said Roman Kovac, Chief Research Officer at.
Many companies are already seeing attacks that exploit vulnerability. Armis told ZDNet that more than a third of its customers (35%) were found to have attempted log4shell attacks. The attackers sometimes target physical servers, virtual servers and IP cameras.
Source: “ZDNet.com”





More Stories
Healing Streams Live Healing Services with Pastor Chris: Miracles Await this March 14th – 16th, 2025!
Essential Care for Hermann’s Tortoise: A Guide to Thriving Pets
Nail Decisions: Which is Better for You, Acrylic or Gel?